Bjqthy Insights
Exploring diverse topics and the latest trends.
Decentralized Fortresses: How to Build Your Safe Haven Online
Discover how to create your own online fortress! Learn essential steps to secure your digital space and protect your privacy.
The Basics of Building a Decentralized Fortress: Your Guide to Online Security
In today's digital age, ensuring your online security is more important than ever. The Basics of Building a Decentralized Fortress begins with understanding the fundamental principles of online protection. One of the primary strategies is to use end-to-end encryption for your communications. This method ensures that only the intended recipient can read your messages, preventing unauthorized access. Additionally, adopting a decentralized approach—where data and applications are distributed across a network rather than stored centrally—can significantly reduce the risk of a single point of failure. Here are some key steps to enhance your online fortress:
- Use strong passwords and a password manager
- Enable two-factor authentication on all accounts
- Stay updated with the latest security patches
Another critical element in building your decentralized fortress is the use of virtual private networks (VPNs) and secure browsers. A VPN encrypts your internet traffic, making it less susceptible to prying eyes, while secure browsers come with built-in privacy features that block trackers and protect your online activities. Furthermore, consider utilizing decentralized storage solutions such as blockchain technology to store sensitive data, as they provide enhanced security and control over your information. Always remember, maintaining online security is not a one-time effort; it requires ongoing vigilance and adjustments to stay ahead of emerging threats.
Counter-Strike is a popular tactical first-person shooter that has garnered a massive following since its initial release. Players are divided into two teams, terrorists and counter-terrorists, competing in various game modes. For players looking to enhance their gaming experience, using a cryptocasino.com promo code can provide exciting rewards and bonuses. Its competitive nature and strategic gameplay have made it a staple in esports events worldwide.
Top Tools and Strategies for Creating Your Digital Safe Haven
In today's digital age, creating your own digital safe haven is essential for protecting your personal information and enhancing your online experience. To start, consider using comprehensive password managers like LastPass or 1Password. These tools not only store your passwords securely but also generate strong passwords for you, minimizing the risk of unauthorized access. Another crucial strategy is to enable two-factor authentication (2FA) on all your accounts. This adds an extra layer of security, requiring not just a password but also a second form of identification, such as a text message or an authentication app.
Beyond securing your accounts, you should also invest in a reliable VPN service like NordVPN or ExpressVPN. A VPN encrypts your internet connection, allowing you to browse the web anonymously and securely. Furthermore, regularly updating your software and apps is vital for protecting against vulnerabilities. Make it a habit to check for updates weekly and run scans with tools like Malwarebytes to keep your devices clean. By combining these tools and strategies, you can create a robust digital safe haven that fosters both security and peace of mind.
Is Your Online Presence Truly Secure? Assessing the Strength of Your Decentralized Fortress
In the digital age, ensuring the security of your online presence is more crucial than ever. A strong decentralized fortress relies on robust security measures that protect personal data and online transactions from various threats. Assessing the strength of your defenses starts with understanding the components of your online presence, including your websites, social media profiles, and email accounts. Consider the following steps to evaluate your security:
- Check the strength of your passwords and consider using password managers.
- Enable two-factor authentication on all platforms.
- Regularly update software to patch vulnerabilities.
- Monitor for suspicious activity across your accounts.
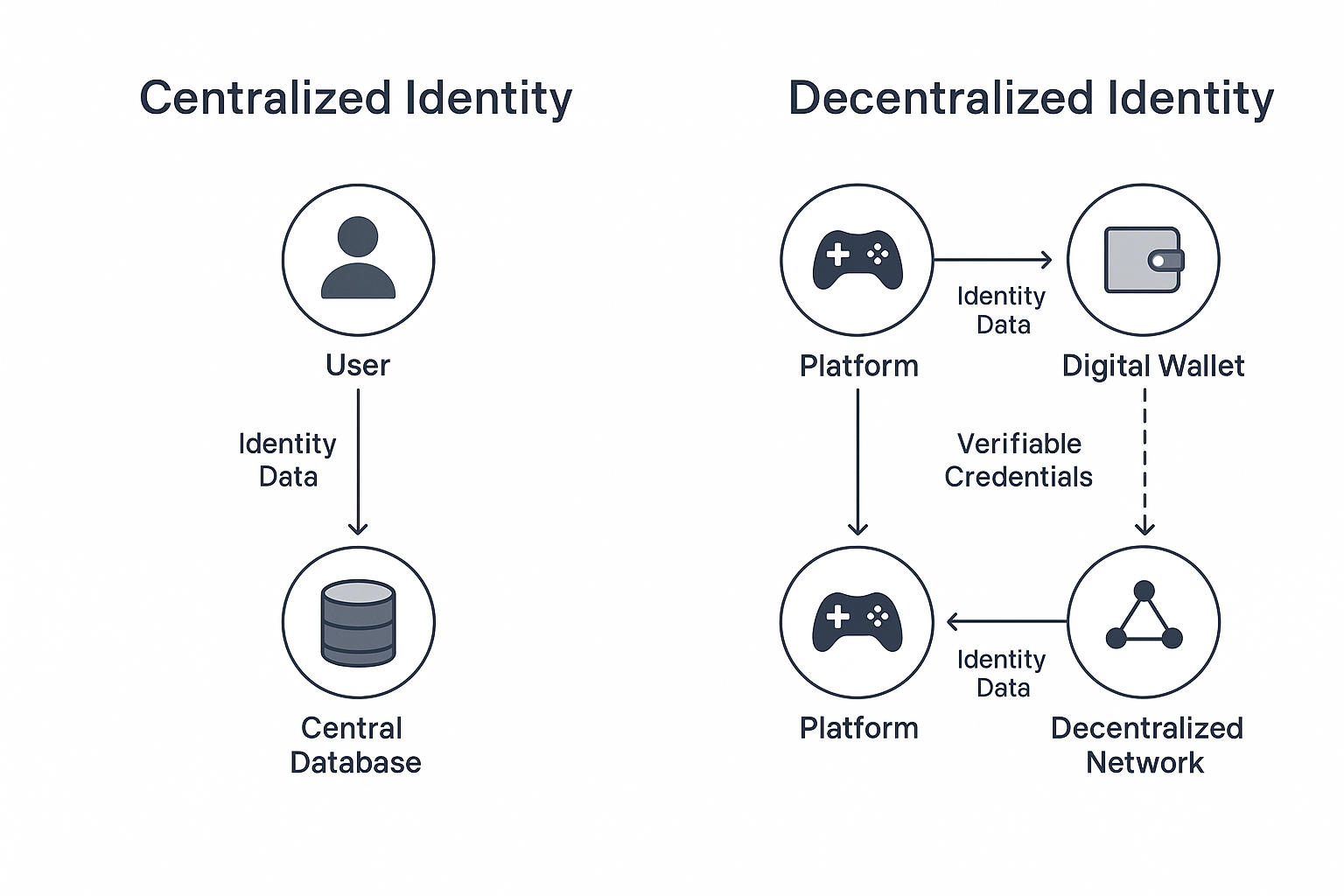
Moreover, understanding the principles of decentralized security can empower you to build a more resilient online identity. Unlike traditional centralized systems, decentralized networks distribute control, making it more challenging for cybercriminals to breach your defenses. This approach provides enhanced security against data breaches and unauthorized access. However, it is essential to stay informed and proactive in your approach to security. Regularly assess your online footprint and identify areas where your defenses may be lacking. Only by acknowledging the vulnerabilities can you fortify your decentralized fortress and safeguard your digital life.